In today's interconnected world, safeguarding our digital footprints has become more crucial than ever. This section delves into the critical issue of unauthorized access to confidential data and the subsequent risks associated with it. Understanding the steps to take when such an event occurs can significantly mitigate the potential harms.
The Unsettling Reality of Unauthorized Data Access
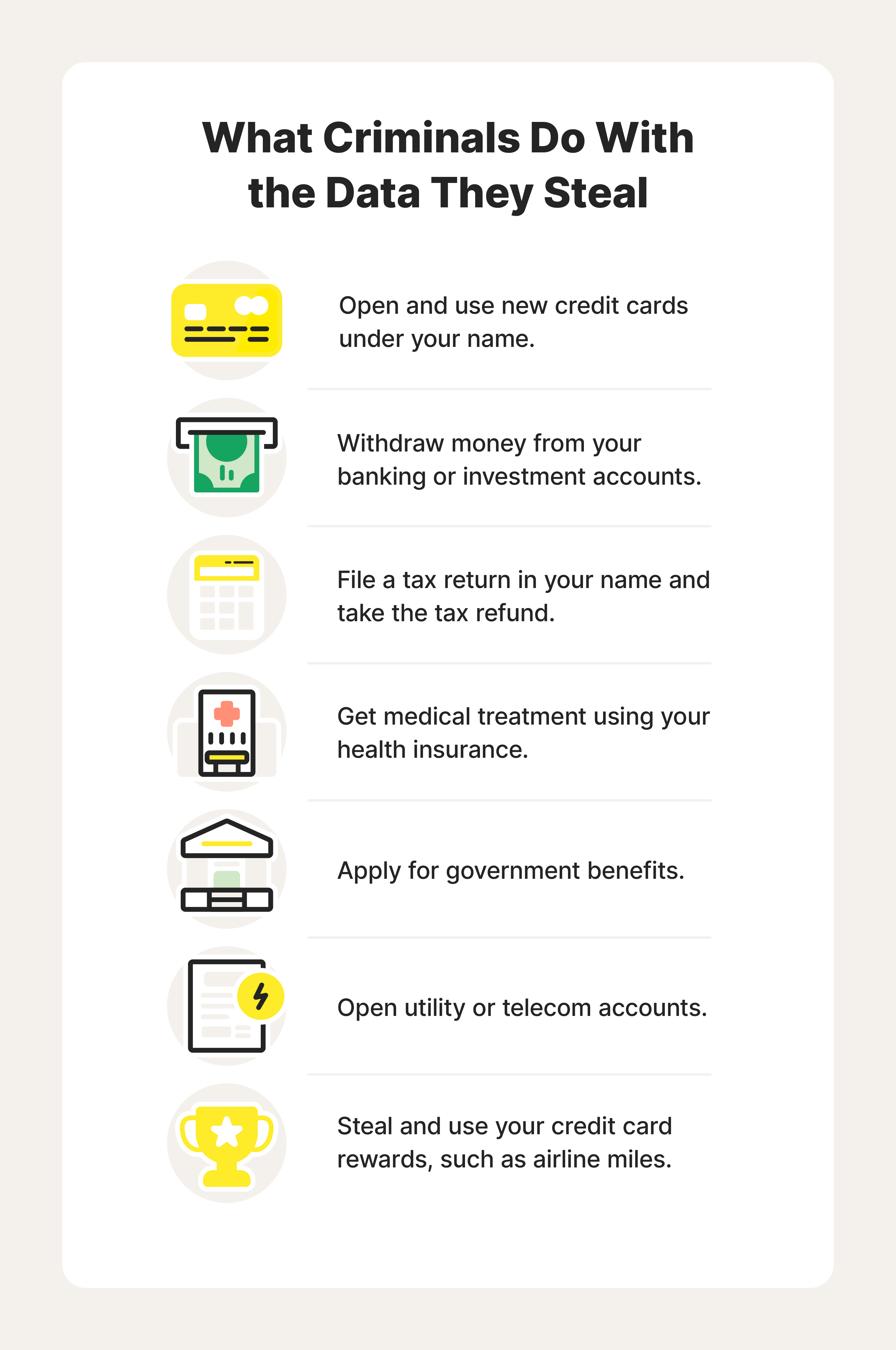
Unauthorized access to sensitive details can lead to a myriad of problems, including the misuse of one's personal credentials. This can result in financial losses, reputational damage, and a host of other complications. It is essential to be proactive in protecting your digital identity and to know how to react when breaches occur.
Immediate Actions Following a Data Exposure Incident
When you suspect that your confidential data has been accessed without authorization, swift action is vital. This includes notifying relevant authorities, changing passwords, and monitoring your financial accounts closely for any unusual activity. Additionally, seeking assistance from cybersecurity experts can provide further protection and guidance.
By staying informed and prepared, individuals can better defend themselves against the fallout from such incidents, ensuring their digital security remains robust in the face of evolving threats.
Understanding Data Breaches and Identity Theft
This section delves into the various tactics employed by malicious actors to infiltrate and exploit sensitive details. By examining these methods, individuals can better comprehend the risks and take proactive steps to safeguard their valuable data.
| Method | Description | Prevention Tips |
|---|---|---|
| Phishing | Deceptive emails or messages designed to trick recipients into revealing confidential details. | Be wary of unsolicited messages, verify sender's authenticity, and avoid clicking on suspicious links. |
| Malware | Software intended to disrupt, damage, or gain unauthorized access to a computer system. | Install reputable antivirus software, keep systems updated, and avoid downloading files from untrusted sources. |
| Password Attacks | Attempts to crack or guess passwords to gain unauthorized access to accounts. | Use strong, unique passwords, enable two-factor authentication, and change passwords regularly. |
| Social Engineering | Manipulative tactics to deceive individuals into divulging sensitive information. | Educate yourself on common social engineering ploys, verify identities before sharing information, and trust your instincts. |
| Unsecured Networks | Using public Wi-Fi networks that lack proper security measures, making them easy targets for interception. | Avoid conducting sensitive transactions on public Wi-Fi, use VPNs for added security, and ensure home networks are secure. |
Understanding these common methods of information compromise is crucial for developing a robust defense strategy. By being aware of these threats, individuals can take the necessary precautions to protect their sensitive data from exploitation.
Common Methods of Information Compromise
This section delves into the various tactics employed by malicious actors to infiltrate and exploit sensitive details. Understanding these methods is crucial for recognizing potential vulnerabilities in one's own security measures.
Phishing Attacks: One of the most prevalent techniques involves deceptive emails or messages that mimic legitimate sources. These communications aim to trick recipients into providing confidential details or clicking on links that install harmful software.
Malware Infections: Software designed to disrupt, damage, or gain unauthorized access to computer systems can be inadvertently downloaded through seemingly innocuous websites or attachments. This malware can silently gather data without the user's knowledge.
Unsecured Networks: Public Wi-Fi networks, often lacking robust security protocols, can be gateways for hackers to intercept communications and access personal accounts. Users are advised to exercise caution when accessing sensitive information over such networks.
Physical Theft: Devices such as laptops, smartphones, and USB drives, if not properly secured, can be physically stolen, providing direct access to the stored data. Encryption and secure storage practices are essential to mitigate this risk.
Insider Threats: Sometimes, the threat comes from within an organization. Disgruntled employees or contractors with access to sensitive data can misuse their privileges, either maliciously or inadvertently, leading to significant leaks.
By being aware of these methods, individuals and organizations can better prepare and implement protective measures to safeguard against unauthorized access and exploitation of their sensitive data.
Signs Your Personal Data May Be at Risk
In this section, we delve into the indicators that might suggest your sensitive details are under threat. Recognizing these signs early can significantly enhance your ability to safeguard your valuable data.
Several telltale signs can alert you to potential unauthorized access to your private details. Below is a table outlining these signs, which can help you take proactive measures to protect your data.
| Sign | Description |
|---|---|
| Unusual Account Activity | If you notice transactions or changes in your account settings that you did not initiate, this could indicate unauthorized access. |
| Unexpected Notifications | Receiving notifications about new account sign-ups or password changes for services you did not request can be a red flag. |
| Declined Cards | Experiencing frequent card declines for legitimate purchases might suggest unauthorized charges or changes to your card information. |
| Spam Emails | An increase in spam or phishing emails could indicate that your email address has been compromised and is being used for malicious activities. |
| Data Leakage Alerts | Receiving alerts from data protection services about potential exposure of your details in known leaks is a clear your name from internet listings sign of risk. |
Being vigilant and monitoring for these signs can help you act swiftly to mitigate risks and protect your sensitive data from further exploitation.
Immediate Steps to Protect Your Identity
In the aftermath of a security incident, swift action is crucial to safeguard your sensitive details. This section outlines essential measures to fortify your defenses and mitigate potential risks associated with unauthorized access to your confidential data.
Upon discovering a breach, follow these immediate steps to enhance your protection:
- Change Passwords: Promptly update all your critical account passwords, ensuring they are robust and unique. Avoid using common phrases or personal information that can be easily guessed.
- Enable Two-Factor Authentication (2FA): Activate 2FA on all applicable accounts. This adds an extra layer of security by requiring a second form of verification, such as a text message or an authentication app.
- Monitor Financial Statements: Regularly check your bank and credit card statements for any unauthorized transactions. Notify your financial institution immediately if you detect any irregularities.
- Alert Credit Bureaus: Contact the major credit bureaus to place a fraud alert on your credit files. This makes it more difficult for someone to open new accounts in your name.
- Use Security Software: Ensure your devices are equipped with up-to-date antivirus and anti-malware software. Regularly scan your devices to detect and remove any malicious software.
- Be Wary of Phishing Attempts: Stay vigilant against suspicious emails or messages that may request personal details or direct you to fraudulent websites. Verify the authenticity of such communications before responding.
Implementing these immediate measures can significantly reduce the impact of a security breach and protect your sensitive data from further exploitation.
Long-Term Strategies for Cybersecurity
In this section, we delve into the enduring tactics that can fortify your digital defenses against unauthorized access and exploitation. These strategies are designed to provide a robust shield over time, ensuring that your sensitive details remain secure from potential threats.
Continuous Monitoring Services: One of the pivotal components of a long-term cybersecurity plan is the utilization of continuous monitoring services. These services actively track any unusual activity related to your financial accounts and alert you to potential issues. By doing so, they help in early detection of unauthorized transactions or changes, which is crucial for mitigating the impact of any security breach.
Role of Credit Monitoring Services: Credit monitoring services play a significant role in this context. They keep a vigilant eye on your credit reports and scores, notifying you of any significant changes. This proactive approach can help you identify and address unauthorized access or fraudulent activities before they escalate into major problems.
Furthermore, these services often include features like identity restoration assistance and insurance against losses due to identity fraud. This comprehensive coverage not only aids in recovery but also provides a financial safety net in the event of a security incident.
To maximize the effectiveness of these services, it is advisable to regularly review the alerts and notifications received. This practice ensures that you are promptly aware of any suspicious activity and can take appropriate action to safeguard your financial integrity.
In conclusion, incorporating credit monitoring services into your cybersecurity strategy is a wise move. It not only enhances your protection but also provides peace of mind, knowing that your financial health is being closely watched by professionals equipped to handle such challenges.
Role of Credit Monitoring Services
This section delves into the pivotal role that credit monitoring services play in safeguarding financial integrity. By continuously tracking and alerting users to changes in their credit profiles, these services offer a proactive defense against unauthorized activities that could undermine financial stability.
Credit monitoring services are designed to:
- Detect unauthorized access to financial records.
- Provide timely alerts regarding suspicious transactions or changes in credit scores.
- Offer detailed reports on credit activities, helping users understand and manage their financial health.
The benefits of utilizing credit monitoring services include:
- Enhanced awareness of financial status, which is crucial for making informed decisions.
- Prevention of fraudulent activities before they escalate into major financial issues.
- Peace of mind, knowing that potential threats are being monitored and addressed promptly.
Choosing the right credit monitoring service involves considering factors such as:
- The comprehensiveness of the monitoring (e.g., credit scores, transaction history).
- The frequency of alerts and updates provided.
- The cost versus the benefits offered by the service.
In conclusion, credit monitoring services are an essential tool in the modern financial landscape. They not only help in mitigating risks associated with unauthorized financial activities but also empower individuals to take control of their financial well-being.
Legal Rights and Resources for Victims
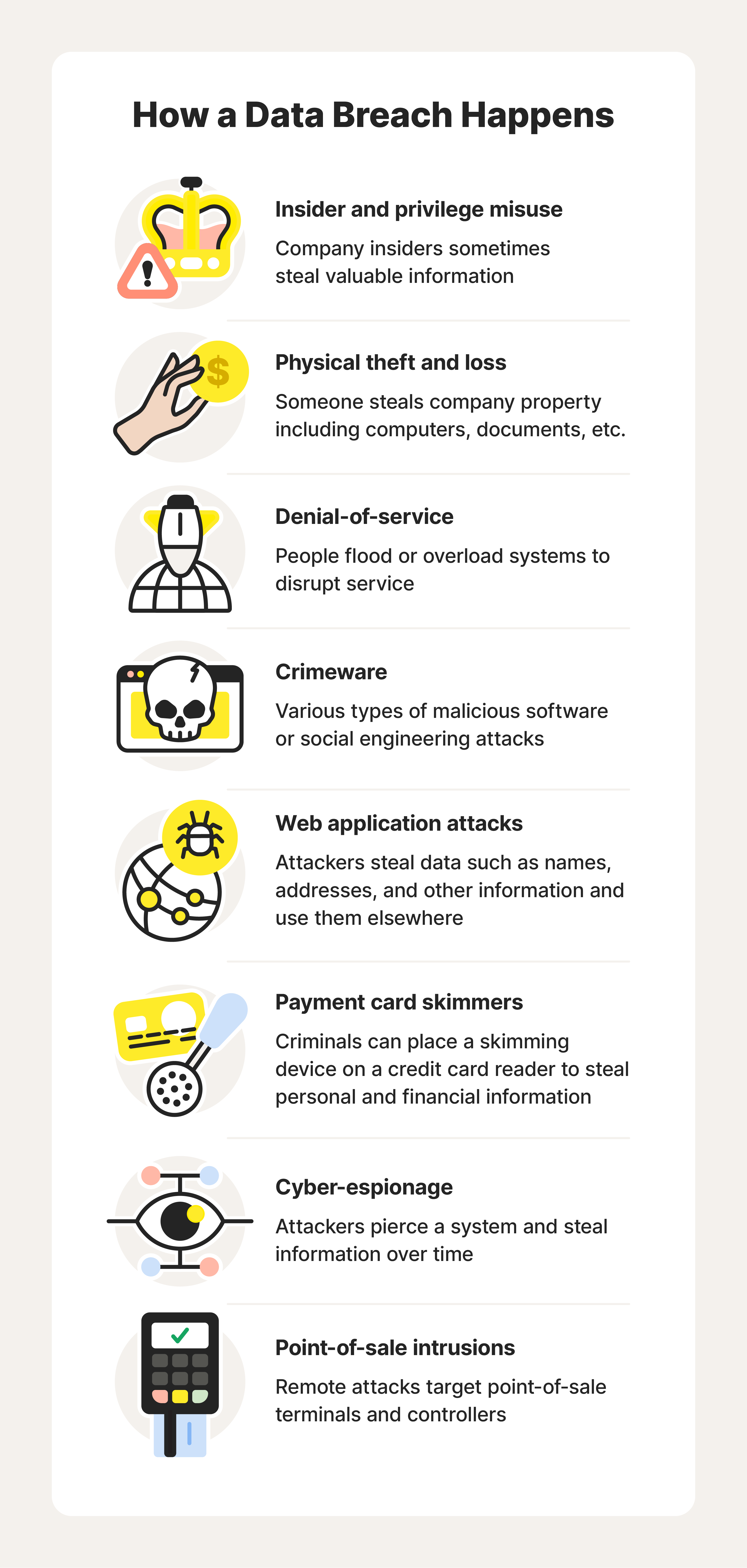
In the aftermath of a security incident involving unauthorized access to sensitive details, it is crucial for affected individuals to understand their entitlements and where to seek assistance. This section outlines the legal protections and support systems available to those who have experienced such an event.
Understanding Your Rights: Victims of unauthorized data access have certain legal protections under both federal and state laws. These rights may include the ability to hold responsible parties accountable, seek compensation for damages, and request corrective actions to prevent further misuse of personal details.
Federal Laws: The Federal Trade Commission (FTC) plays a pivotal role in safeguarding consumer rights. The FTC provides guidance on how to report incidents and offers resources to help individuals protect their personal details from further exploitation. Additionally, the FTC can assist in resolving disputes and may impose penalties on entities that fail to adequately protect sensitive consumer data.
State Laws: Many states have their own regulations that offer additional protections for residents. These laws often provide specific procedures for reporting incidents and may offer more comprehensive remedies for victims. It is important to familiarize oneself with the laws of the state in which you reside.
Seeking Legal Assistance: For those who have been affected by unauthorized access to their sensitive details, consulting with a legal professional can be invaluable. Attorneys specializing in privacy law can provide advice on the best course of action, help navigate the complexities of legal proceedings, and represent victims in seeking justice and compensation.
Support Organizations: Various non-profit organizations and government agencies are dedicated to assisting individuals who have experienced unauthorized access to their sensitive details. These organizations offer educational materials, counseling services, and advocacy support to help victims recover and prevent future incidents.
In conclusion, understanding the legal framework and available resources is essential for anyone who has been a victim of unauthorized access to their sensitive details. By leveraging these rights and resources, individuals can take proactive steps towards recovery and enhance their personal security measures.
Preventative Measures for Future Protection
In this section, we delve into proactive strategies aimed at fortifying your digital defenses against potential threats. By implementing robust measures, individuals can significantly reduce the likelihood of falling victim to malicious activities online.
Education and Awareness play a pivotal role in safeguarding against digital vulnerabilities. Understanding the common tactics used by cybercriminals is the first step towards prevention. Regular updates on the latest scams and security practices can empower users to make informed decisions.
Strong Passwords are a fundamental yet often overlooked aspect of digital security. Utilizing a combination of letters, numbers, and special characters can enhance the impenetrability of your accounts. Additionally, employing different passwords for various platforms can prevent a domino effect in case one account is compromised.
Two-Factor Authentication (2FA) adds an extra layer of security by requiring a second form of verification, such as a text message or biometric data, in addition to the password. This method significantly reduces the risk of unauthorized access even if the password is compromised.
Regularly Updating Software is crucial as it often includes patches for discovered vulnerabilities. Neglecting updates can leave systems exposed to known threats. Automating these updates can ensure that your devices are always equipped with the latest security enhancements.
Secure Internet Practices involve being cautious about the websites you visit and the links you click. Avoiding suspicious emails and websites can prevent malware from infiltrating your devices. Additionally, using secure and reputable internet connections can further protect your data.
Lastly, Regular Monitoring of Financial Statements and Credit Reports can help detect any unauthorized activity early. Prompt action upon noticing discrepancies can minimize the damage and prevent further exploitation.

